Users of Cleo-managed file transfer software are being urged to ensure that their instances are not exposed to the internet […]
Internet traffic grew hugely in 2024, with Google taking the strain
(Image credit: Lesterman / Shutterstock) Internet traffic rose by 17% year-over-year in 2024, Cloudflare finds Google.com and Chrome maintain significant […]
Fake Recruiters Distribute Banking Trojan via Malicious Apps in Phishing Scam
Cybersecurity researchers have shed light on a sophisticated mobile phishing (aka mishing) campaign that’s designed to distribute an updated version […]
The Future of Network Security: Automated Internal and External Pentesting
Dec 10, 2024The Hacker NewsVulnerability / Perimeter Security In today’s rapidly evolving threat landscape, safeguarding your organization against cyberattacks is […]
Phone Phishing Gang Busted: Eight Arrested in Belgium and Netherlands
Dec 10, 2024Ravie LakshmananCybercrime / Vishing Belgian and Dutch authorities have arrested eight suspects in connection with a “phone phishing” […]
Hackers Weaponize Visual Studio Code Remote Tunnels for Cyber Espionage
A suspected China-nexus cyber espionage group has been attributed to an attacks targeting large business-to-business IT service providers in Southern […]
Ongoing Phishing and Malware Campaigns in December 2024
Dec 10, 2024The Hacker NewsMalware Analysis / Cyber Threat Cyber attackers never stop inventing new ways to compromise their targets. […]
Don’t buy a router, buy a fast and secure ASUS WiFi 7 extendable router
(Image credit: Asus) Now that there’s a larger selection of WiFi 7 devices from mainstream mobile phones such as iPhone […]
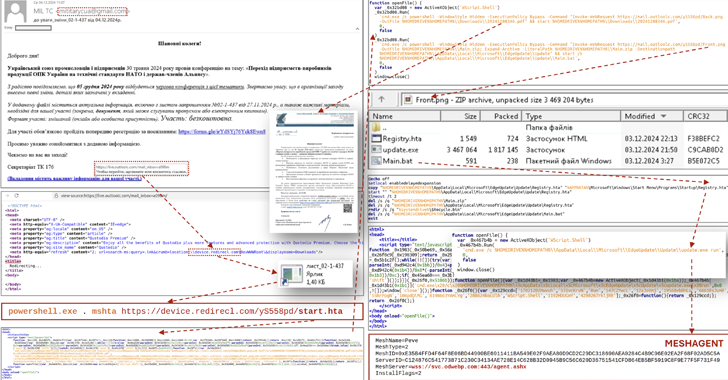
CERT-UA Warns of Phishing Attacks Targeting Ukraine’s Defense and Security Force
Dec 10, 2024Ravie LakshmananMalware / Cyber Attack The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new […]
How AI is Enhancing Cloud Performance and Cost Optimization?
Artificial Intelligence (AI) transforms cloud infrastructures, bringing unprecedented efficiency, scalability, and performance. As businesses increasingly adopt cloud environments to manage […]