(Image credit: Future) Lenovo is known for its extensive range of laptops and unwavering quality. They are also manufacturers of […]
Nvidia RTX 5000 prediction suggests RTX 5090 will be a monster flagship GPU… but it’s the RTX 5070 I’m worried about
(Image credit: Future / John Loeffler) Expectation for Nvidia RTX 5090 is a 60% to 70% gen-on-gen uplift RTX 5070 […]
Microsoft Recall offers a ‘sensitive information filter’ to avoid saving your credit card details – but whoops, it doesn’t work
(Image credit: Shutterstock / Kostenko Maxim) Microsoft’s ‘Recall’ feature for Windows has been mired in controversy over privacy concerns The […]
Intel and AMD may have another desktop competitor – Qualcomm is supposedly working on a new Snapdragon X Elite Gen 2 desktop CPU
Image Credit: Qualcomm (Image credit: Qualcomm) A new suggestion from a reliable leaker hints at Qualcomm’s new CPU heading to […]
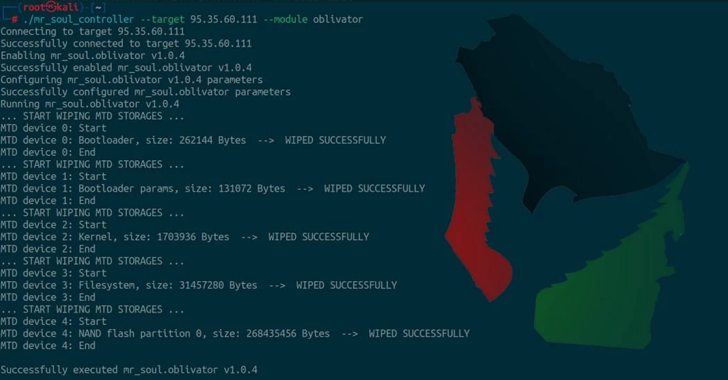
Iran-Linked IOCONTROL Malware Targets SCADA and Linux-Based IoT Platforms
Dec 13, 2024The Hacker NewsIoT Security / Operational Technology Iran-affiliated threat actors have been linked to a new custom malware […]
Windows 11’s ‘suggested actions’ feature is headed to the Microsoft Graveyard – but here’s what’s replacing it
Microsoft is deprecating Windows 11’s “Suggested Actions” menu, introduced in 2022 A new AI-powered tool, “Click to Do,” will replace […]
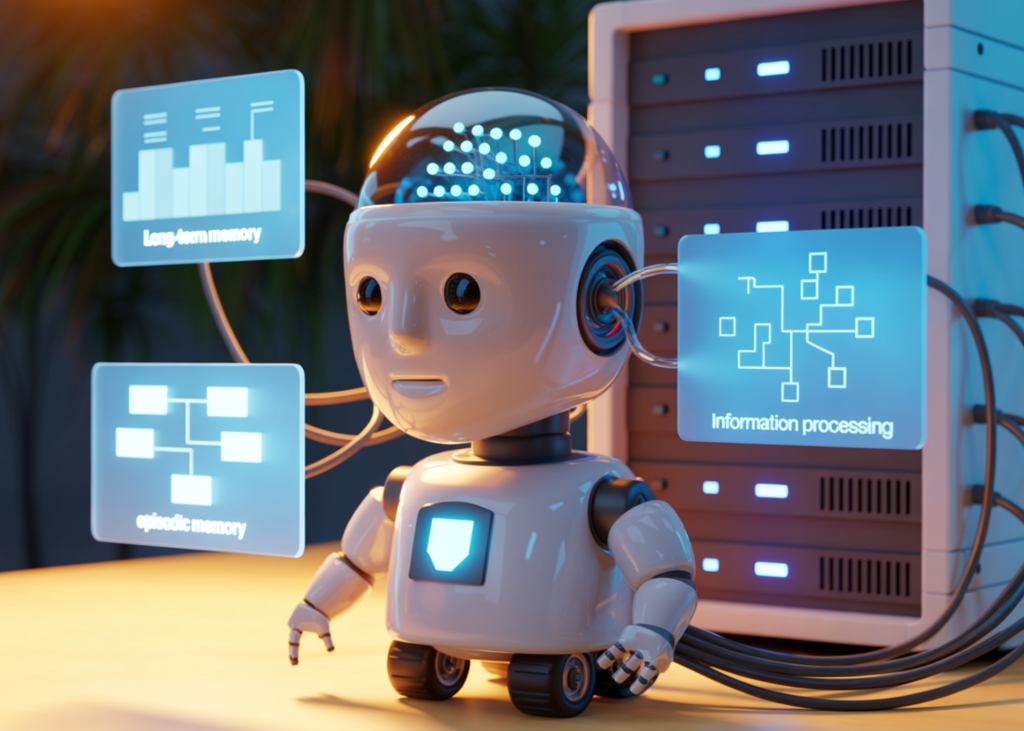
How to Generate a CrowdStrike RFM Report With AI in Tines
Run by the team at orchestration, AI, and automation platform Tines, the Tines library contains pre-built workflows shared by real […]
Nvidia cranks RTX 5000 GPU hype machine up to full speed, teasing ‘GeForce at CES 2025’ as Witcher 4 trailer drops a big hint
(Image credit: Gigabyte) Nvidia has teased revelations about ‘GeForce at CES 2025’ This must surely be next-gen GPUs, likely the […]
Keynote, Pages, and Numbers just got way better with this free Apple Intelligence update – here’s how
Apple’s iWork suite is available for iOS/iPadOS devices and macOS. (Image credit: Apple) Apple has updated its iWork suite of […]
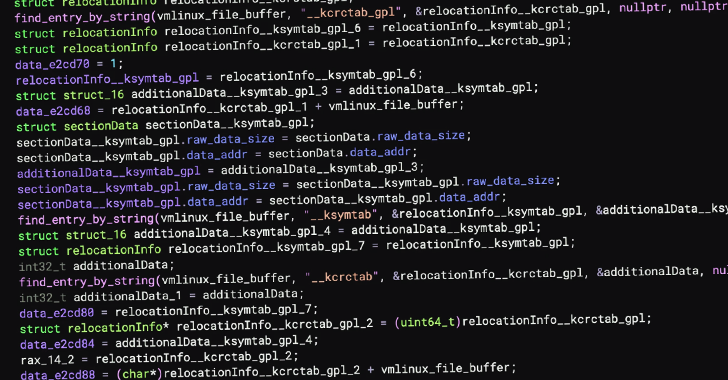
New Linux Rootkit PUMAKIT Uses Advanced Stealth Techniques to Evade Detection
Dec 13, 2024Ravie LakshmananLinux / Threat Analysis Cybersecurity researchers have uncovered a new Linux rootkit called PUMAKIT that comes with […]