Social media has seen a 335 percent boom in new scams using deepfake videos and company-branded posts to lure victims […]
Data Governance in DevOps: Ensuring Compliance in the AI Era
With the evolution of modern software development, CI/CD pipeline governance has emerged as a critical factor in maintaining both agility […]
Yes, there is a way to get a vertical taskbar in Windows 11
One of the changes in Windows 11 that continues to generate lots of complaining is the removal of a vertical […]
New Investment Scam Leverages AI, Social Media Ads to Target Victims Worldwide
Dec 16, 2024Ravie LakshmananCryptocurrency / Phishing Attack Cybersecurity researchers are calling attention to a new kind of investment scam that […]
Building trust in telemetry data [Q&A]
With the increasing importance of observability in digital operations, businesses need to ensure the reliability and relevance of their telemetry […]
New Glutton Malware Exploits Popular PHP Frameworks Like Laravel and ThinkPHP
Cybersecurity researchers have discovered a new PHP-based backdoor called Glutton that has been put to use in cyber attacks targeting […]
Optimizing Data Strategy: Databricks in Modern Analytics
In the era of big data, organizations are continuously seeking powerful tools to analyze, visualize, and extract insights from their […]
Ukrainian Minors Recruited for Cyber Ops and Reconnaissance in Russian Airstrikes
Dec 16, 2024Ravie LakshmananCyber Attack / Cyber Espionage The Security Service of Ukraine (SBU or SSU) has exposed a novel […]
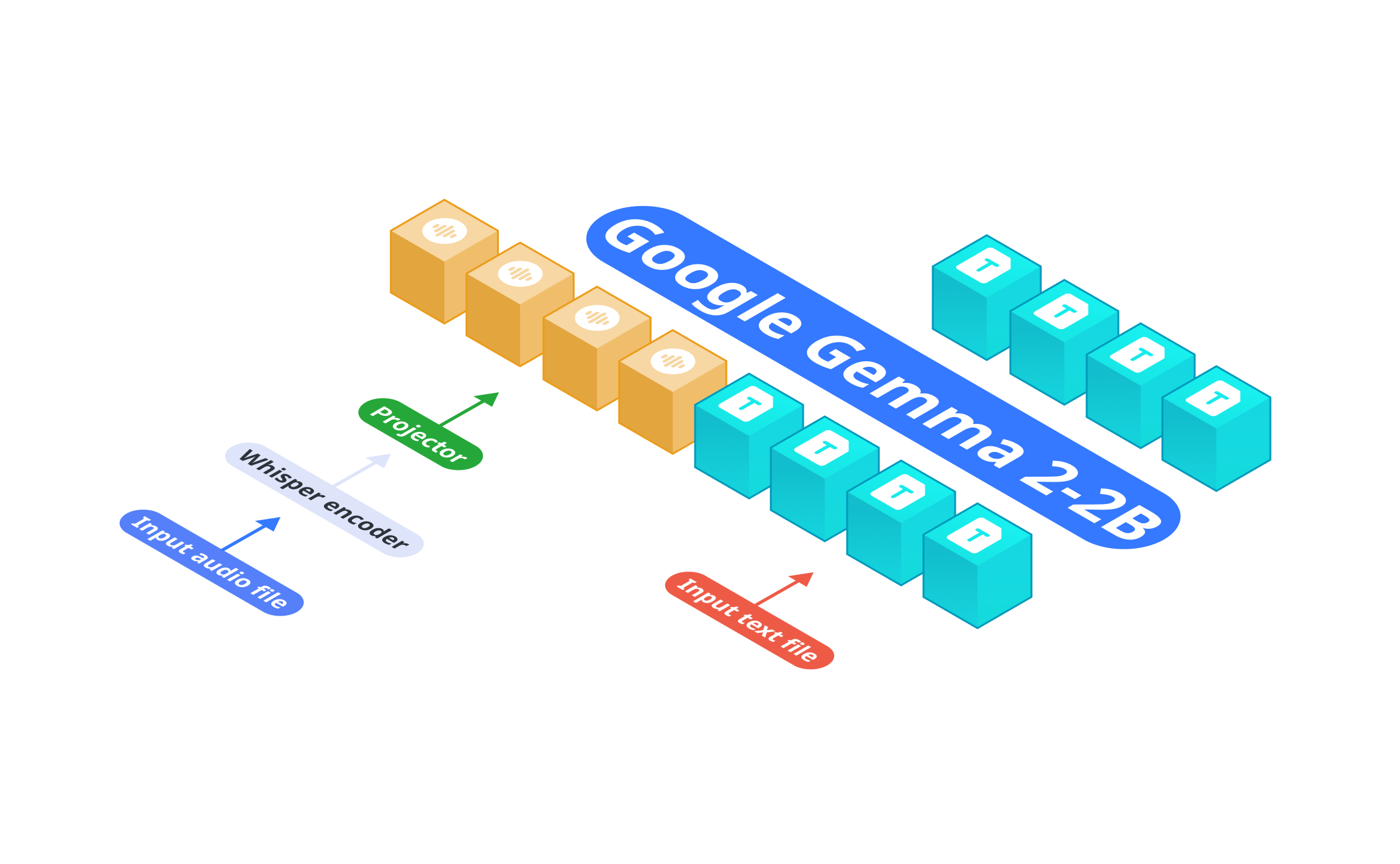
Nexa AI Releases OmniAudio-2.6B: A Fast Audio Language Model for Edge Deployment
Audio language models (ALMs) play a crucial role in various applications, from real-time transcription and translation to voice-controlled systems and […]
DeepSeek-AI Open Sourced DeepSeek-VL2 Series: Three Models of 3B, 16B, and 27B Parameters with Mixture-of-Experts (MoE) Architecture Redefining Vision-Language AI
Integrating vision and language capabilities in AI has led to breakthroughs in Vision-Language Models (VLMs). These models aim to process […]








![Building trust in telemetry data [Q&A]](https://thetechbriefs.com/wp-content/uploads/2024/12/528-building-trust-in-telemetry-data-qa.jpg)