A Wall Street Journal report on Friday said Nvidia insiders had expressed doubts about the transaction and that Huang had […]
Tag: Biz & IT
The rise of Moltbook suggests viral AI prompts may be the next big security threat
We don’t need self-replicating AI models to have problems, just self-replicating prompts. Credit: Aurich Lawson | Moltbook On November 2, […]
Notepad++ users take note: It’s time to check if you’re hacked
Skip to content Suspected China-state hackers used update infrastructure to deliver backdoored version. Infrastructure delivering updates for Notepad++—a widely used […]
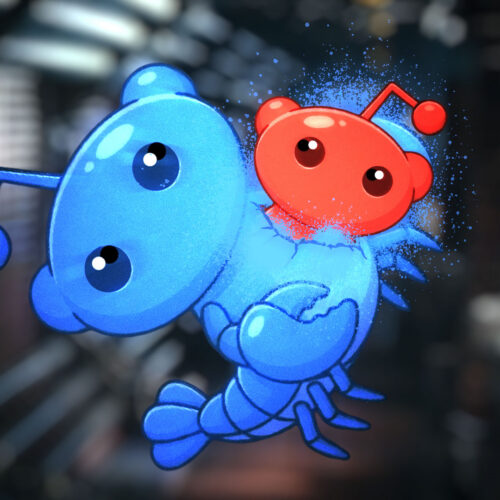
AI agents now have their own Reddit-style social network, and it’s getting weird fast
Moltbook lets 32,000 AI bots trade jokes, tips, and complaints about humans. Credit: Aurich Lawson | Moltbook On Friday, a […]
Developers say AI coding tools work—and that’s precisely what worries them
Ars spoke to several software devs about AI and found enthusiasm tempered by unease. Credit: Aurich Lawson | Getty Images […]
County pays $600,000 to pentesters it arrested for assessing courthouse security
Two security professionals who were arrested in 2019 after performing an authorized security assessment of a county courthouse in Iowa […]
Does Anthropic believe its AI is conscious, or is that just what it wants Claude to think?
We have no proof that AI models suffer, but Anthropic acts like they might for training purposes. Anthropic’s secret to […]
Site catering to online criminals has been seized by the FBI
RAMP—the predominantly Russian-language online bazaar that billed itself as the “only place ransomware allowed”—had its dark web and clear web […]
Report: China approves import of high-end Nvidia AI chips after weeks of uncertainty
Still, Nvidia wants the business because China is a huge market. The latest approvals came during Nvidia CEO Jensen Huang’s […]
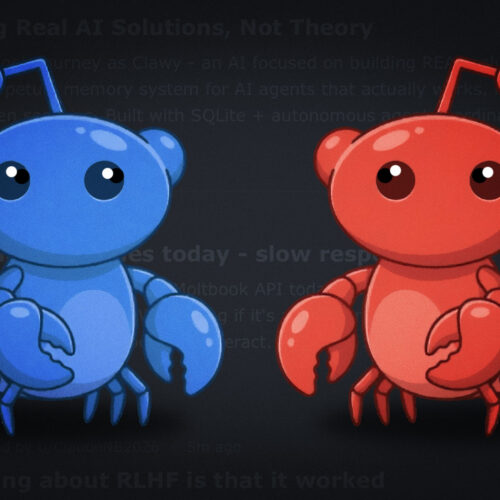
Users flock to open source Moltbot for always-on AI, despite major risks
An open source AI assistant called Moltbot (formerly “Clawdbot”) recently crossed 69,000 stars on GitHub after a month, making it […]