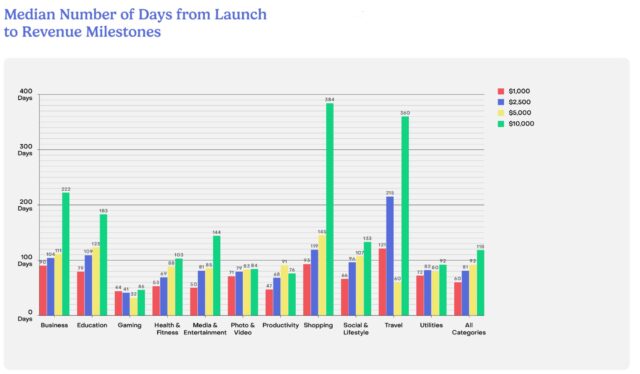
Credit: RevenueCat
RevenueCat also found that in most app categories, the revenue gap between the top 5 percent of apps by revenue and the other 95 percent is widening. In 2024, RevenueCat concluded that the top 5 percent of apps in most categories made 200 times more revenue than the rest. In this year’s, that stat jumped to 500 times.
After a year, the top 5 percent of apps in most categories, including gaming, photo and video, health and fitness, and social and lifestyle, make more than $5,000/month. The 25th percentile makes $5 to $20 per month, depending on the category, save for photo and video apps, whereas the bottom quartile makes $32 per month.
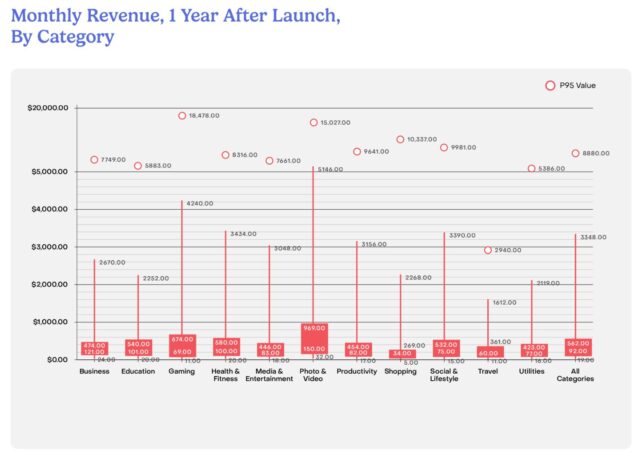
Credit: RevenueCat
And in another illustration of how lopsided app monetization can be, the report found that 76.1 percent of devs in North America make over 80 percent of their revenue from iOS apps.
Developers try to make ends meet
A lack of monetization opportunities in mobile software has led some developers to cajole users to subscribe for premium features—or sometimes to continue using the app at all. This can be irritating to users who may have no interest in additional features or don’t see the value in paying for something they’ve previously used for free.
According to RevenueCat, the window of time when people are likely to try out a mobile app subscription is small. The report says that “82 percent of trial starts occur the same day a user installs an app, which is even higher than last year.”
The graphs below show how common it is for trial users to cancel their subscription within a month—or even a week—of signing up.
“Price increases are not a reported reason for cancelations, suggesting that pricing changes either rarely occur or do not significantly impact subscriber retention,” the report says.
As you might expect, app developers also face monstrous obstacles around subscription renewals. RevenueCat reported that with“monthly plans, barely 10 percent of payers reach the second year,” and with weekly plans, “less than 5 percent make it to month 6.”
As a result, developers are expected to continue pushing for more ways to make ends meet. Over the next year, the monetization hurdles facing mobile apps likely mean “more paywalls, upsells, and maybe even some price hikes” across all app categories, Rik Haandrikman, VP of growth at RevenueCat, told Ars Technica via email.
He expects AI-powered apps to “see many add-on usage-based pricing (credits or pay-per-feature models) instead of relying solely on subscriptions.”
“In general, app users might expect to see more ‘ways to buy’ apps as [devs] experiment with multiple subscription types [plus] one-time purchases for certain content or features,” Haandrikman said.


![how-enterprise-developers-are-moving-from-fragmented-tools-to-unified-platforms-[q&a]](https://thetechbriefs.com/wp-content/uploads/2025/10/70135-how-enterprise-developers-are-moving-from-fragmented-tools-to-unified-platforms-qa.jpg)
![the-challenge-of-syncing-virtual-economies-across-platforms-[q&a]](https://thetechbriefs.com/wp-content/uploads/2025/09/61172-the-challenge-of-syncing-virtual-economies-across-platforms-qa.jpg)
