Ravie LakshmananJan 20, 2026Malware / Threat Intelligence Cybersecurity researchers have uncovered a new phishing campaign that exploits social media private […]
Category: Hackers
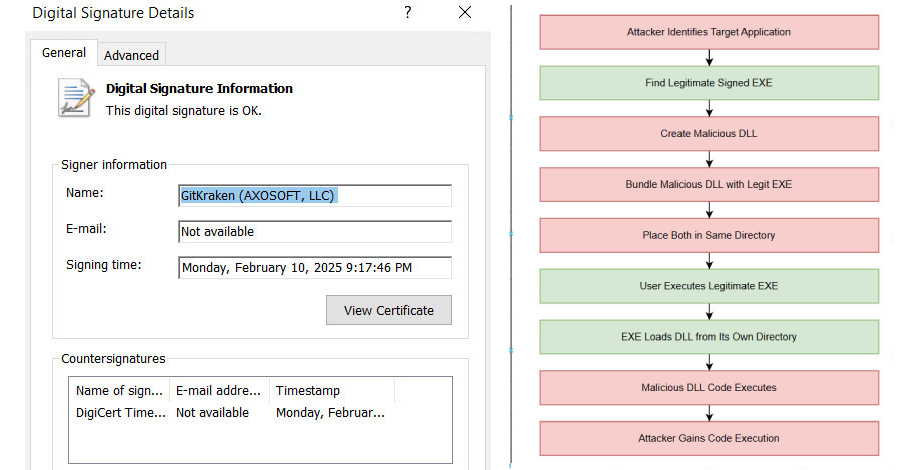
Hackers Exploit c-ares DLL Side-Loading to Bypass Security and Deploy Malware
Security experts have disclosed details of an active malware campaign that’s exploiting a DLL side-loading vulnerability in a legitimate binary […]
Hackers Hijack Blender 3D Assets to Deploy StealC V2 Data-Stealing Malware
Nov 25, 2025Ravie LakshmananMalware / Browser Security Cybersecurity researchers have disclosed details of a new campaign that has leveraged Blender […]
Hackers Weaponize Windows Hyper-V to Hide Linux VM and Evade EDR Detection
Nov 06, 2025Ravie LakshmananMalware / Network Security The threat actor known as Curly COMrades has been observed exploiting virtualization technologies […]
Hackers Used Snappybee Malware and Citrix Flaw to Breach European Telecom Network
Oct 21, 2025Ravie LakshmananCyber Espionage / Network Security A European telecommunications organization is said to have been targeted by a […]
Hackers Abuse Blockchain Smart Contracts to Spread Malware via Infected WordPress Sites
A financially motivated threat actor codenamed UNC5142 has been observed abusing blockchain smart contracts as a way to facilitate the […]
Hackers Deploy Linux Rootkits via Cisco SNMP Flaw in “Zero Disco’ Attacks
Oct 16, 2025Ravie LakshmananVulnerability / Linux Cybersecurity researchers have disclosed details of a new campaign that exploited a recently disclosed […]
Hackers Target ICTBroadcast Servers via Cookie Exploit to Gain Remote Shell Access
Oct 15, 2025Ravie LakshmananVulnerability / Server Security Cybersecurity researchers have disclosed that a critical security flaw impacting ICTBroadcast, an autodialer […]
Hackers Turn Velociraptor DFIR Tool Into Weapon in LockBit Ransomware Attacks
Oct 11, 2025Ravie LakshmananNetwork Security / Vulnerability Threat actors are abusing Velociraptor, an open-source digital forensics and incident response (DFIR) […]
Hackers Access SonicWall Cloud Firewall Backups, Spark Urgent Security Checks
Oct 09, 2025Ravie LakshmananCloud Security / Network Security SonicWall on Wednesday disclosed that an unauthorized party accessed firewall configuration backup […]