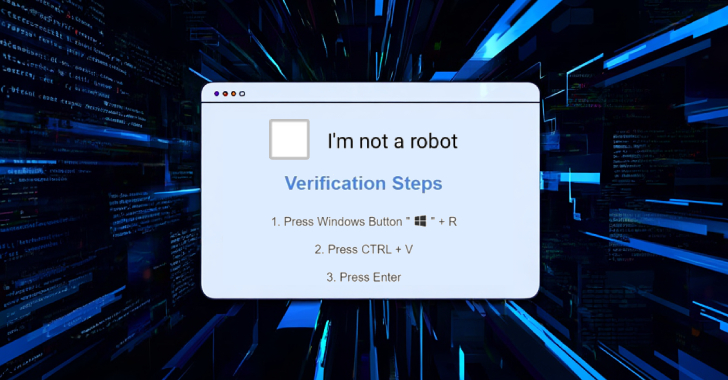
Jan 02, 2026Ravie LakshmananCloud Security / Email Security Cybersecurity researchers have disclosed details of a phishing campaign that involves the […]
Category: Cybercriminals
Cybercriminals Exploit Remote Monitoring Tools to Infiltrate Logistics and Freight Networks
Nov 03, 2025Ravie LakshmananCybercrime / Supply Chain Attack Bad actors are increasingly training their sights on trucking and logistics companies […]
Cybercriminals turn to stealth to bypass malware detection
A new report reveals a 40 percent (quarter-over-quarter) increase in evasive, advanced malware. The data highlights encrypted channels as adversaries’ […]
Cybercriminals Exploit X’s Grok AI to Bypass Ad Protections and Spread Malware to Millions
Sep 04, 2025Ravie LakshmananArtificial Intelligence / Malware Cybersecurity researchers have flagged a new technique that cybercriminals have adopted to bypass […]
Cybercriminals Deploy CORNFLAKE.V3 Backdoor via ClickFix Tactic and Fake CAPTCHA Pages
Aug 21, 2025Ravie LakshmananMalware / Cryptocurrency Threat actors have been observed leveraging the deceptive social engineering tactic known as ClickFix […]
Cybercriminals Use Fake Apps to Steal Data and Blackmail Users Across Asia’s Mobile Networks
Cybersecurity researchers have discovered a new, large-scale mobile malware campaign that’s targeting Android and iOS platforms with fake dating, social […]
“No honor among thieves”: M&S hacking group starts turf war
Genevieve Stark, head of cybercrime analysis at Google Threat Intelligence Group, said DragonForce could be attempting to attract RansomHub’s affiliates. […]
Cybercriminals turn to “residential proxy” services to hide malicious traffic
For years, gray market services known as “bulletproof” hosts have been a key tool for cybercriminals looking to anonymously maintain […]
Cybercriminals Target AI Users with Malware-Loaded Installers Posing as Popular Tools
Fake installers for popular artificial intelligence (AI) tools like OpenAI ChatGPT and InVideo AI are being used as lures to […]
Cybercriminals Clone Antivirus Site to Spread Venom RAT and Steal Crypto Wallets
May 27, 2025Ravie LakshmananMalware / Cybersecurity Cybersecurity researchers have disclosed a new malicious campaign that uses a fake website advertising […]