The infamous hacking group ShinyHunters has released to the dark web millions of data records claimed to have been stolen from SoundCloud, Crunchbase and Betterment.
Although the data is yet to be verified, the numbers claimed in the leaks do match up with data breaches of the three named companies in recent months. In all, there are around 52 millions records involved.
In a post to his LinkedIn account, Alon Gal – the Co-Founder & CTO at Hudson Rock – writes: “BIG – ShinyHunters confirmed to me that they are behind the recent Okta vishing campaign and have published alleged data from three major victims (Crunchbase, SoundCloud, and Betterment) on their new blog, stating more are coming”.
He goes on to say:
I was approached by ShinyHunters following a BleepingComputer report yesterday about an Okta SSO vishing campaign that resulted in several unknown victims. ShinyHunters confirmed they were behind the campaign and shared a Tor victims blog in which Crunchbase, SoundCloud, and Betterment all had their alleged data leaked after rejecting the group’s extortion attempt. The group said more victims will be published soon.
I only downloaded the Crunchbase data so far. It shows databases with PII, signed contracts, and other corporate data belonging to the company.
Sharing more more in the way of detail, Gal says:
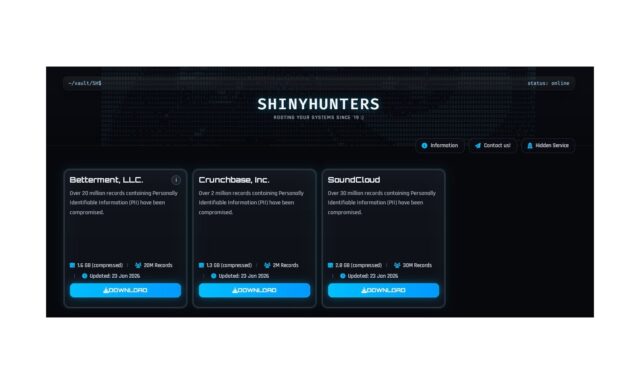
These are the descriptions added to each company –
Betterment, LLC.
Over 20 million records containing Personally Identifiable Information (PII) have been compromised.
Crunchbase, Inc.
Over 2 million records containing Personally Identifiable Information (PII) have been compromised.
SoundCloud
Over 30 million records containing Personally Identifiable Information (PII) have been compromised.
Researchers looking to get the URL, please DM me.
To learn how to protect yourself from being a victim of this campaign, please read Okta’s advisory – https://lnkd.in/dTRBY2yH
The data leak appears to be linked to a vishing campaign highlighted by Okta Threat Intelligence. While the security firm does not make reference to the data leak, it warns:
Okta Threat Intelligence has detected and dissected multiple custom phishing kits that have evolved to meet the specific needs of voice-based social engineers (“callers”) in vishing campaigns.
These custom kits are made available on an as-a-service basis and are increasingly used by a growing number of intrusion actors targeting Google, Microsoft, Okta and a range of cryptocurrency providers.
The kits are capable of intercepting the credentials of targeted users, while also presenting the supporting context required to convince users to approve MFA challenges, or to take other actions in the interests of the attacker on the phone. They can be adapted on the fly by callers to control what pages are presented in the user’s browser, in order to sync with the caller’s script and whatever legitimate MFA challenges the caller is presented with as they attempt to sign-in.
With ShinyHunters already having claimed responsibility for such attacks, it seems reasonable to link the two events.



