Dec 12, 2024Ravie LakshmananMobile Security / Cyber Espionage The Russia-linked state-sponsored threat actor tracked as Gamaredon has been attributed to […]
Category: Security
Researchers Uncover Symlink Exploit Allowing TCC Bypass in iOS and macOS
Dec 12, 2024Ravie LakshmananVulnerability / Device Security Details have emerged about a now-patched security vulnerability in Apple’s iOS and macOS […]
SaaS Budget Planning Guide for IT Professionals
SaaS services are one of the biggest drivers of OpEx (operating expenses) for modern businesses. With Gartner projecting $247.2 billion […]
WordPress Hunk Companion Plugin Flaw Exploited to Silently Install Vulnerable Plugins
Dec 12, 2024Ravie LakshmananWebsite Security / Vulnerability Malicious actors are exploiting a critical vulnerability in the Hunk Companion plugin for […]
Europol Dismantles 27 DDoS Attack Platforms Across 15 Nations; Admins Arrested
Dec 12, 2024Ravie LakshmananCyber Crime / DDoS Attack A global law enforcement operation has failed 27 stresser services that were […]
Secret Blizzard Deploys Kazuar Backdoor in Ukraine Using Amadey Malware-as-a-Service
Dec 11, 2024Ravie LakshmananMalware / Cyber Espionage The Russian nation-state actor tracked as Secret Blizzard has been observed leveraging malware […]
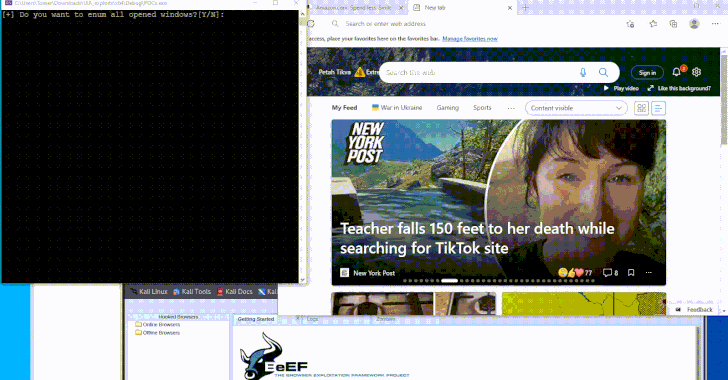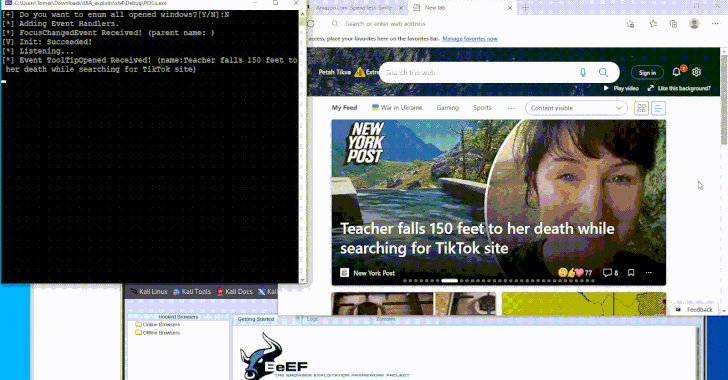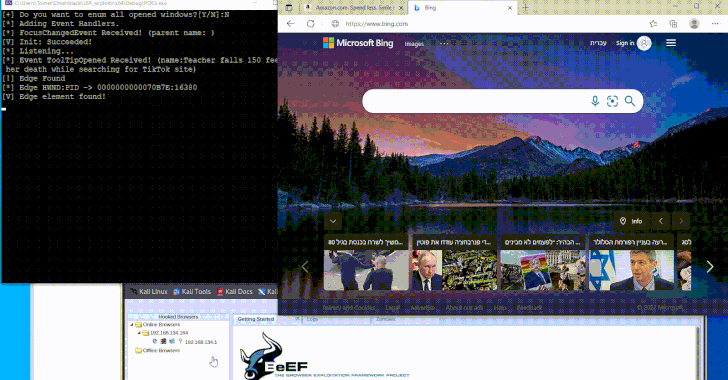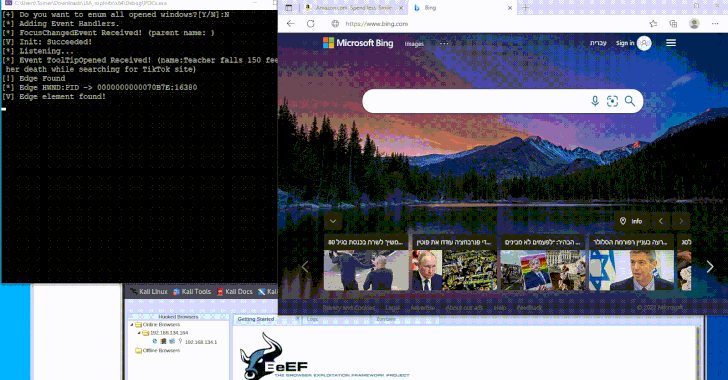
New Malware Technique Could Exploit Windows UI Framework to Evade EDR Tools
Dec 11, 2024Ravie LakshmananMalware / Endpoint Security A newly devised technique leverages a Windows accessibility framework called UI Automation (UIA) […]
Microsoft MFA AuthQuake Flaw Enabled Unlimited Brute-Force Attempts Without Alerts
Dec 11, 2024Ravie LakshmananVulnerability / Authentication Cybersecurity researchers have flagged a “critical” security vulnerability in Microsoft’s multi-factor authentication (MFA) implementation […]
ZLoader Malware Returns With DNS Tunneling to Stealthily Mask C2 Comms
Dec 11, 2024Ravie LakshmananRansomware / Malware Cybersecurity researchers have discovered a new version of the ZLoader malware that employs a […]
Chinese EagleMsgSpy Spyware Found Exploiting Mobile Devices Since 2017
Cybersecurity researchers have discovered a novel surveillance program that’s suspected to be used by Chinese police departments as a lawful […]