Cybersecurity researchers have shed light on a sophisticated mobile phishing (aka mishing) campaign that’s designed to distribute an updated version […]
Category: Security
The Future of Network Security: Automated Internal and External Pentesting
Dec 10, 2024The Hacker NewsVulnerability / Perimeter Security In today’s rapidly evolving threat landscape, safeguarding your organization against cyberattacks is […]
Phone Phishing Gang Busted: Eight Arrested in Belgium and Netherlands
Dec 10, 2024Ravie LakshmananCybercrime / Vishing Belgian and Dutch authorities have arrested eight suspects in connection with a “phone phishing” […]
Hackers Weaponize Visual Studio Code Remote Tunnels for Cyber Espionage
A suspected China-nexus cyber espionage group has been attributed to an attacks targeting large business-to-business IT service providers in Southern […]
Ongoing Phishing and Malware Campaigns in December 2024
Dec 10, 2024The Hacker NewsMalware Analysis / Cyber Threat Cyber attackers never stop inventing new ways to compromise their targets. […]
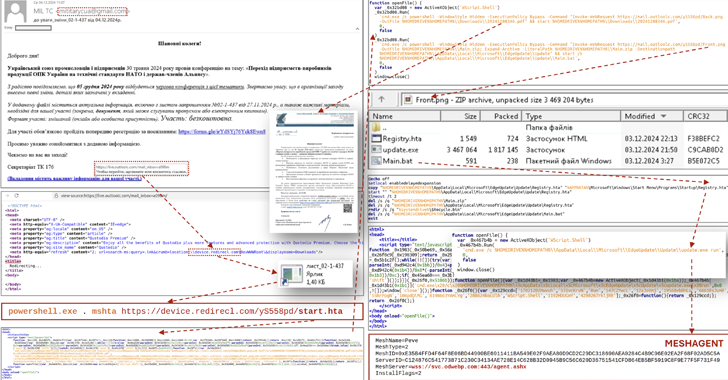
CERT-UA Warns of Phishing Attacks Targeting Ukraine’s Defense and Security Force
Dec 10, 2024Ravie LakshmananMalware / Cyber Attack The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new […]
Black Basta Ransomware Evolves with Email Bombing, QR Codes, and Social Engineering
Dec 09, 2024Ravie LakshmananThreat Intelligence / Malware The threat actors linked to the Black Basta ransomware have been observed switching […]
⚡ THN Recap: Top Cybersecurity Threats, Tools and Tips (Dec 2 – 8)
Dec 09, 2024Ravie LakshmananCyber Threats / Weekly Recap This week’s cyber world is like a big spy movie. Hackers are […]
Researchers Uncover Prompt Injection Vulnerabilities in DeepSeek and Claude AI
Dec 09, 2024Ravie LakshmananArtificial Intelligenc / Vulnerability Details have emerged about a now-patched security flaw in the DeepSeek artificial intelligence […]
Seven Bolt-Ons to Make Your Entra ID More Secure for Critical Sessions
Identity security is all the rage right now, and rightfully so. Securing identities that access an organization’s resources is a […]