A suspected China-nexus cyber espionage group has been attributed to an attacks targeting large business-to-business IT service providers in Southern […]
Category: Security
Ongoing Phishing and Malware Campaigns in December 2024
Dec 10, 2024The Hacker NewsMalware Analysis / Cyber Threat Cyber attackers never stop inventing new ways to compromise their targets. […]
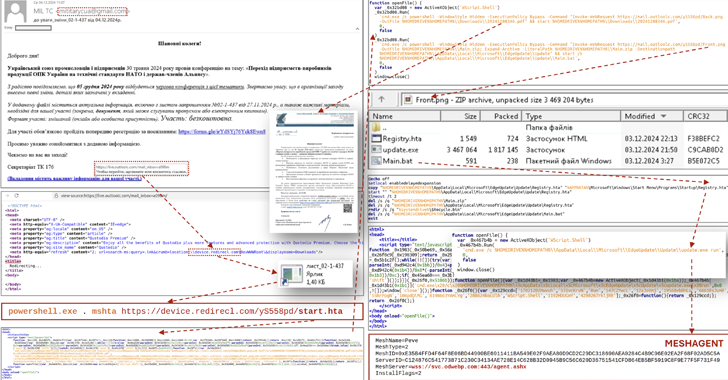
CERT-UA Warns of Phishing Attacks Targeting Ukraine’s Defense and Security Force
Dec 10, 2024Ravie LakshmananMalware / Cyber Attack The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new […]
Black Basta Ransomware Evolves with Email Bombing, QR Codes, and Social Engineering
Dec 09, 2024Ravie LakshmananThreat Intelligence / Malware The threat actors linked to the Black Basta ransomware have been observed switching […]
⚡ THN Recap: Top Cybersecurity Threats, Tools and Tips (Dec 2 – 8)
Dec 09, 2024Ravie LakshmananCyber Threats / Weekly Recap This week’s cyber world is like a big spy movie. Hackers are […]
Researchers Uncover Prompt Injection Vulnerabilities in DeepSeek and Claude AI
Dec 09, 2024Ravie LakshmananArtificial Intelligenc / Vulnerability Details have emerged about a now-patched security flaw in the DeepSeek artificial intelligence […]
Seven Bolt-Ons to Make Your Entra ID More Secure for Critical Sessions
Identity security is all the rage right now, and rightfully so. Securing identities that access an organization’s resources is a […]
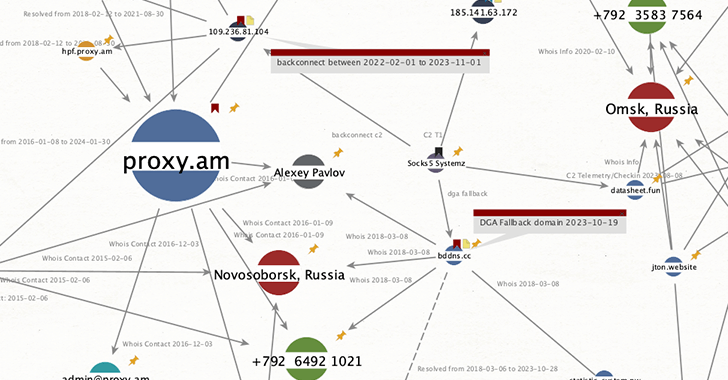
Socks5Systemz Botnet Powers Illegal Proxy Service with 85,000+ Hacked Devices
A malicious botnet called Socks5Systemz is powering a proxy service called PROXY.AM, according to new findings from Bitsight. “Proxy malware […]
Ultralytics AI Library Compromised: Cryptocurrency Miner Found in PyPI Versions
Dec 07, 2024Ravie LakshmananSupply Chain Attack / Cryptocurrency In yet another software supply chain attack, it has come to light […]
Learn How Experts Secure Privileged Accounts—Proven PAS Strategies Webinar
Dec 07, 2024The Hacker NewsEnterprise Security / Threat Prevention Cybercriminals know that privileged accounts are the keys to your kingdom. […]