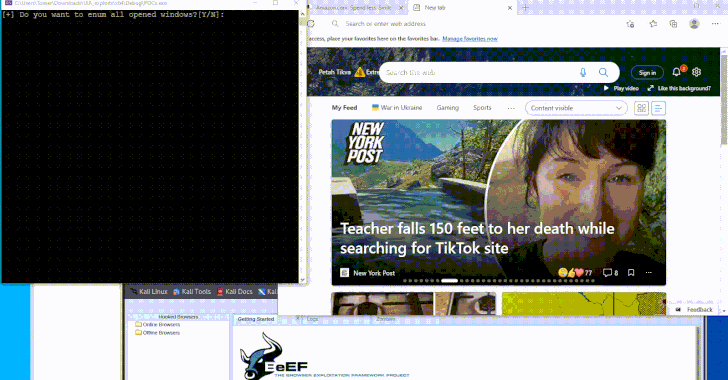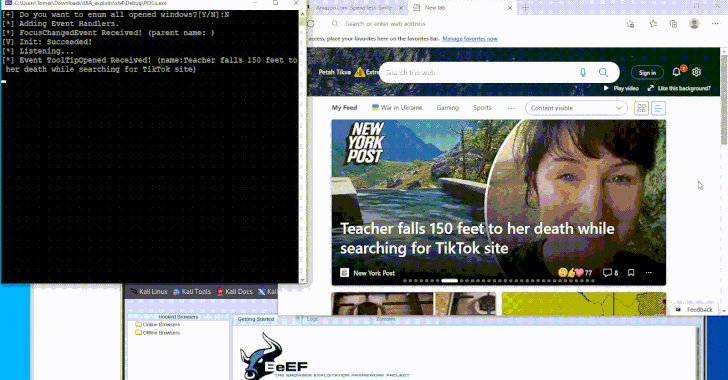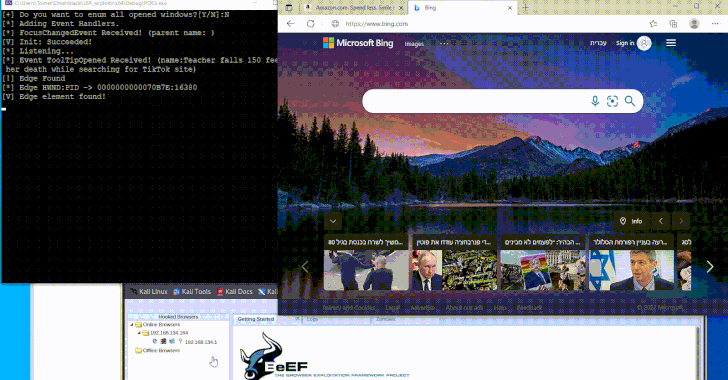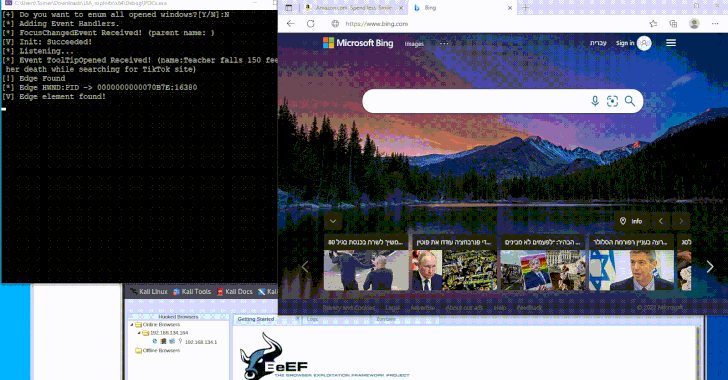
Dec 11, 2024Ravie LakshmananMalware / Endpoint Security A newly devised technique leverages a Windows accessibility framework called UI Automation (UIA) […]
Author: Admin
Microsoft MFA AuthQuake Flaw Enabled Unlimited Brute-Force Attempts Without Alerts
Dec 11, 2024Ravie LakshmananVulnerability / Authentication Cybersecurity researchers have flagged a “critical” security vulnerability in Microsoft’s multi-factor authentication (MFA) implementation […]
These are the best Chrome Extensions of 2024 – according to Google
(Image credit: Google) Google has announced its 12 favorite Chrome Extensions of 2024 There are extensions for productivity, shopping, and […]
ZLoader Malware Returns With DNS Tunneling to Stealthily Mask C2 Comms
Dec 11, 2024Ravie LakshmananRansomware / Malware Cybersecurity researchers have discovered a new version of the ZLoader malware that employs a […]
Apple names the 17 apps you should download now – here are the 2024 App Store Awards winners
(Image credit: Apple / Kino / NYT / Moises) Just about three weeks after Apple revealed the 45 finalists in […]
Chinese EagleMsgSpy Spyware Found Exploiting Mobile Devices Since 2017
Cybersecurity researchers have discovered a novel surveillance program that’s suspected to be used by Chinese police departments as a lawful […]
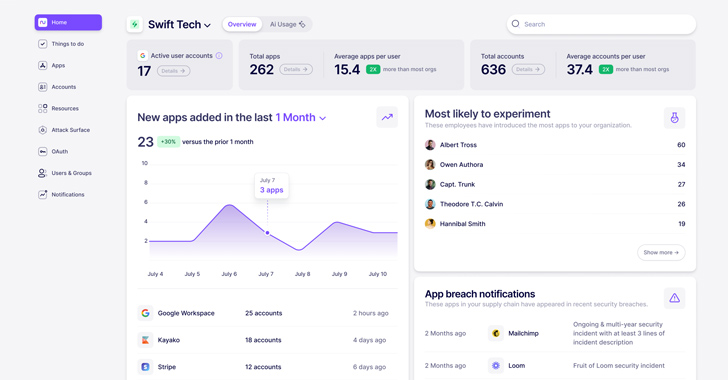
What is Nudge Security and How Does it Work?
In today’s highly distributed workplace, every employee has the ability to act as their own CIO, adopting new cloud and […]
Researchers Uncover Espionage Tactics of China-Based APT Groups in Southeast Asia
Dec 11, 2024Ravie LakshmananCyber Espionage / Cyber Attack A suspected China-based threat actor has been linked to a series of […]
Broadcom Loses another Major VMware Customer Beeks Group’s Bold Move: From VMware to Open Nebula
UK-based Fintech cloud operator Beeks Group has chosen to migrate from VMware to the open-source Open Nebula platform, which counts […]
Microsoft Fixes 72 Flaws, Including Patch for Actively Exploited CLFS Vulnerability
Microsoft closed out its Patch Tuesday updates for 2024 with fixes for a total of 72 security flaws spanning its […]